AWS IoT
Overview
This tutorial demonstrates how Mongoose Library can be used to communicate with the AWS IoT service. We create an MQTT client that:
- Connects to the AWS IoT MQTT server
- When connected, subscribes to the topic
d/rx. Any message received on that topic, gets logged - Publishes message
helloto thed/txevery second
AWS IoT is an MQTT 3.1.1 service that uses two-way TLS for authentication - see SSL/TLS tutorial for TLS background. Two way TLS means that instead of using a traditional user/password to authenticate, AWS IoT uses TLS certificates. Before connecting, AWS IoT needs a "thing" to be registered, and for that "thing", a TLS certificate gets created. That certificate gets copied to a device and used as a "password" to authenticate with AWS IoT. Also, AWS IoT attaches a "policy" to every certificate which says what capabilities a "thing" has.
The MQTT standard does not regulate access rights for clients. For example, any client can subscribe to a wildcard topic # and sniff all messages sent by any client. That is too dangerous for a production system. Therefore, commercial services like AWS IoT invent their ways to restrict access for clients. AWS IoT uses "policies", which is a JSON document that describes access rules - like, which topics a given client can send to, and which topics it can subscribe to. Once created, policies can be attached (referenced by) certificates.
To summarize, the following steps should be performed in order to connect to an AWS IoT service:
- Login to AWS IoT, get your domain URL
- Create an AWS IoT policy
- Create an EC private key and a CSR (Certificate Signing Request) type "make csr", see Makefile
- Create your certificate in AWS; download certificates
- Attach your certificate to our policy
- Register your AWS IoT thing and associate it to your certificate
- Configure the MQTT client to use certificates for 2-way TLS, and your domain
Get your domain URL
- Click "Settings" on the left bar, then "View domain configuration", and copy the domain, we'll use it to change
s_urllater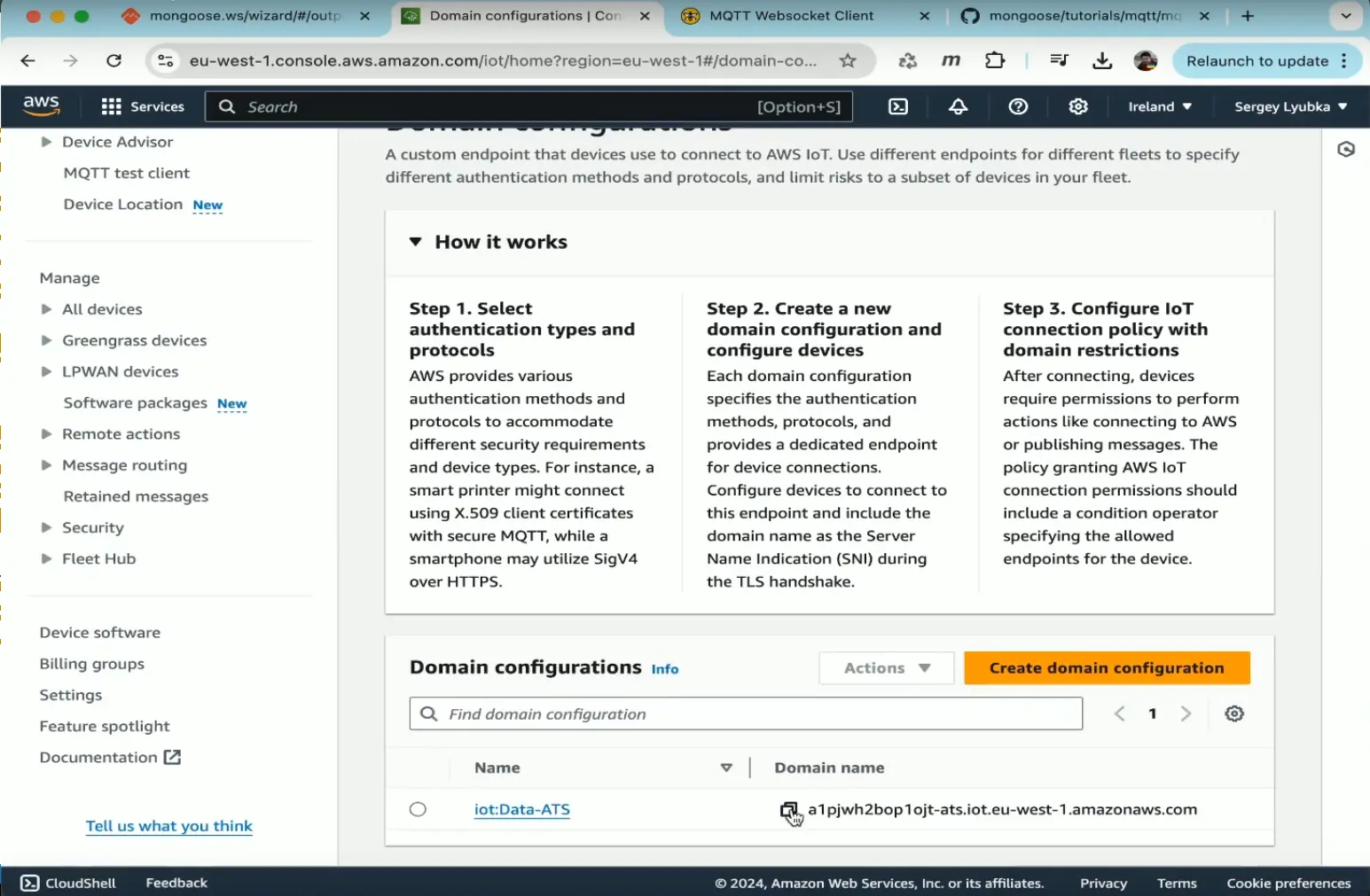
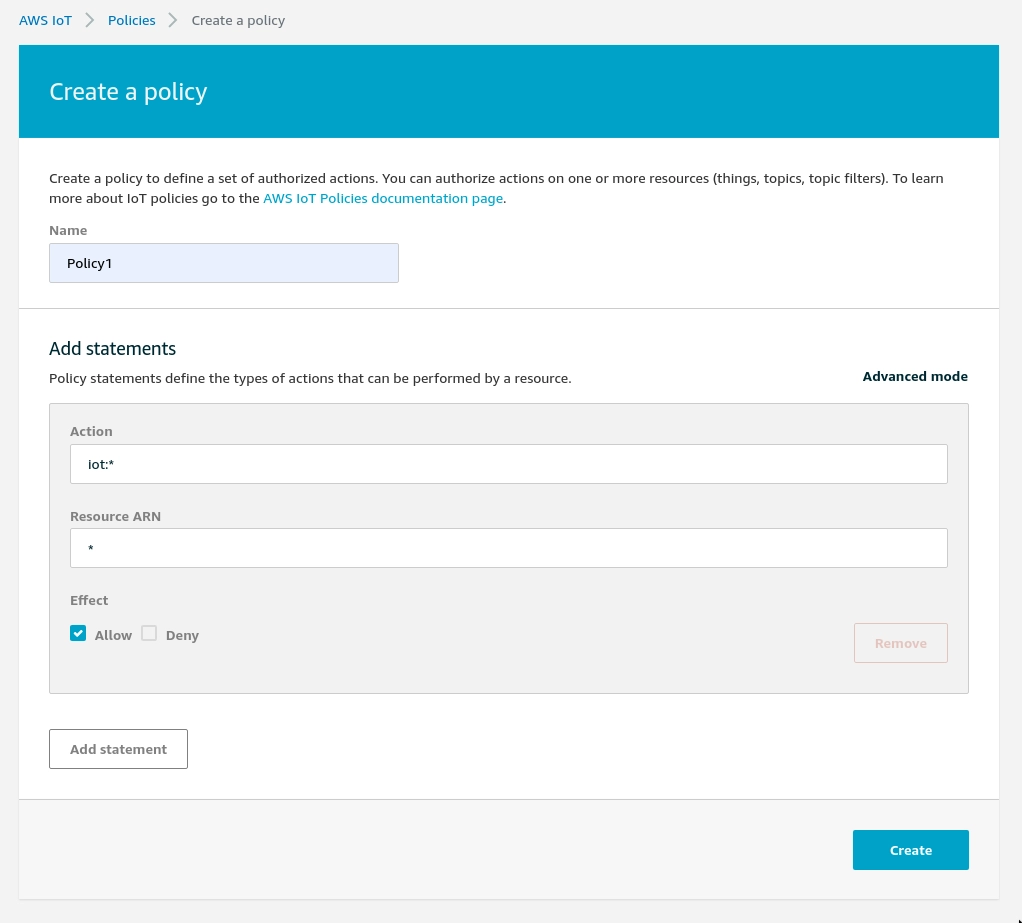
Create an AWS IoT policy
- On the left bar, click on "Security"
- then click on "Policies"
- On the right pane, click on "Create"
- Fill in the fields the following way:
- Name : PolicyAllow
- Action : iot:*
- Resource ARN: *
- Effect : allow
- then, click "Create"
Create EC private key and CSR
- You need to have OpenSSL installed. Start a terminal in the project directory; clone the Mongoose Library repo, and go into the example directory:
$ git clone https://github.com/cesanta/mongoose $ cd mongoose/tutorials/mqtt/mqtt-client-aws-iot - type "make csr"
$ make csr openssl ecparam -noout -name prime256v1 -genkey -out key.pem openssl req -new -key key.pem -subj /CN=Mongoose -out crt.csr - Your key is in
key.pem, your Certificate Sign Request is incrt.csr
Create and download AWS certificates
- On the left bar, click on "Security"
- then click on "Certificates"
- On the right pane, click on "Add Certificate", then select "Create Certificate"
- Choose "Create certificate with certificate signing request (CSR)"
- Upload your Certificate Sign Request, choose
crt.csr, created on the previous step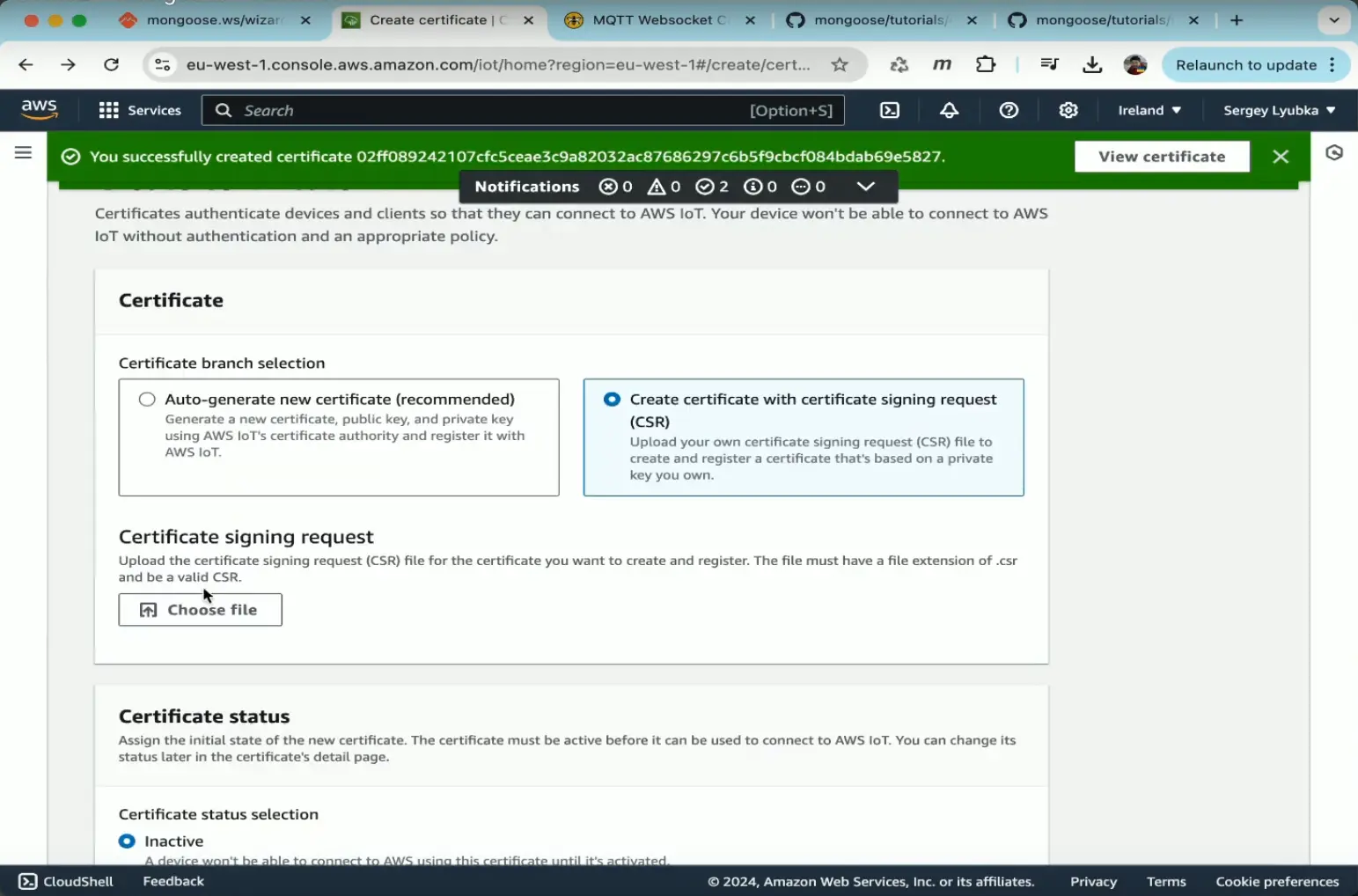
- Choose "Active" to activate the certificate
- Click Create
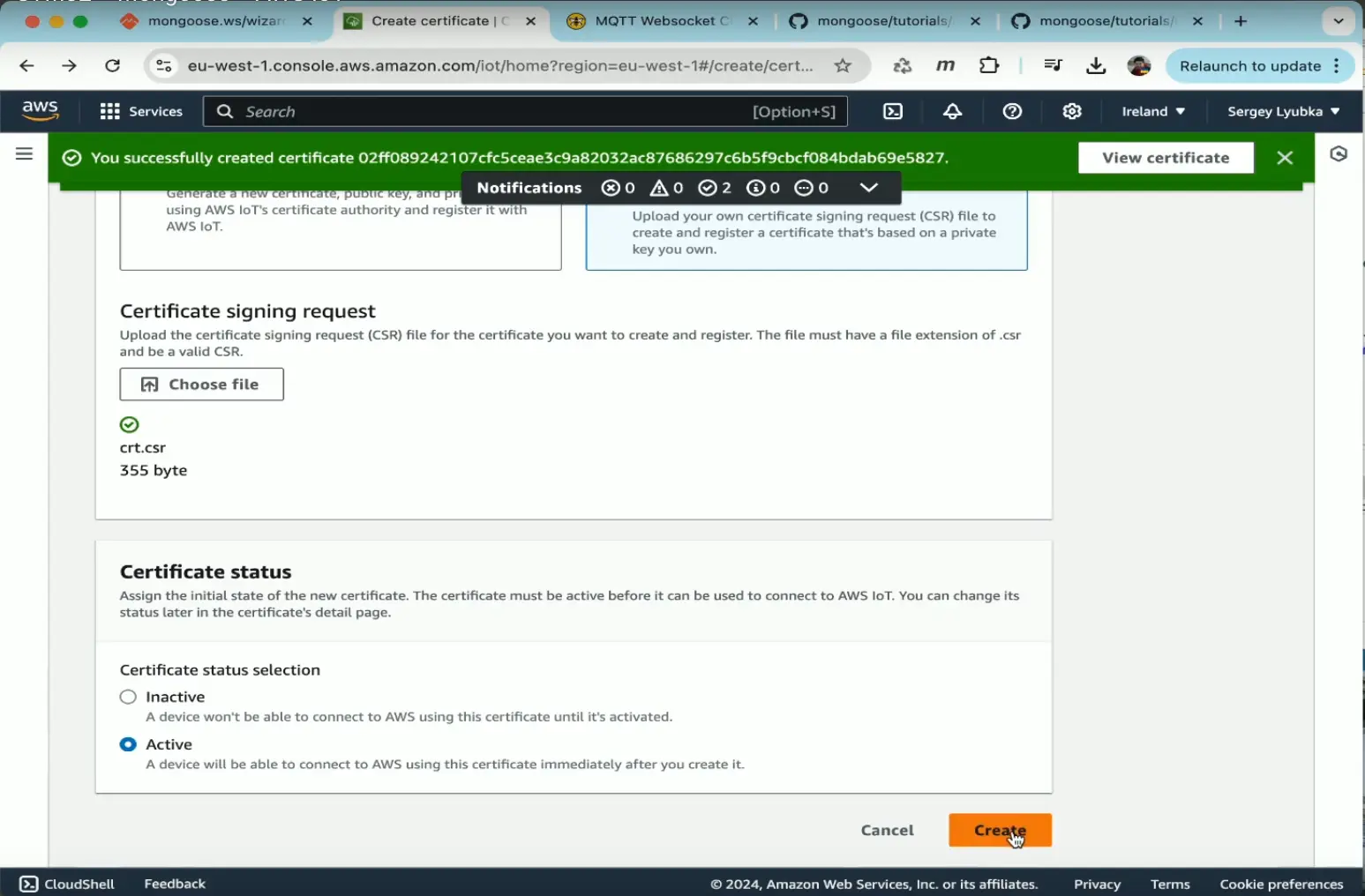
- In the dialog box that appears, download
AmazonRootCA1.pemasca.pemand the generated certificate ascrt.pem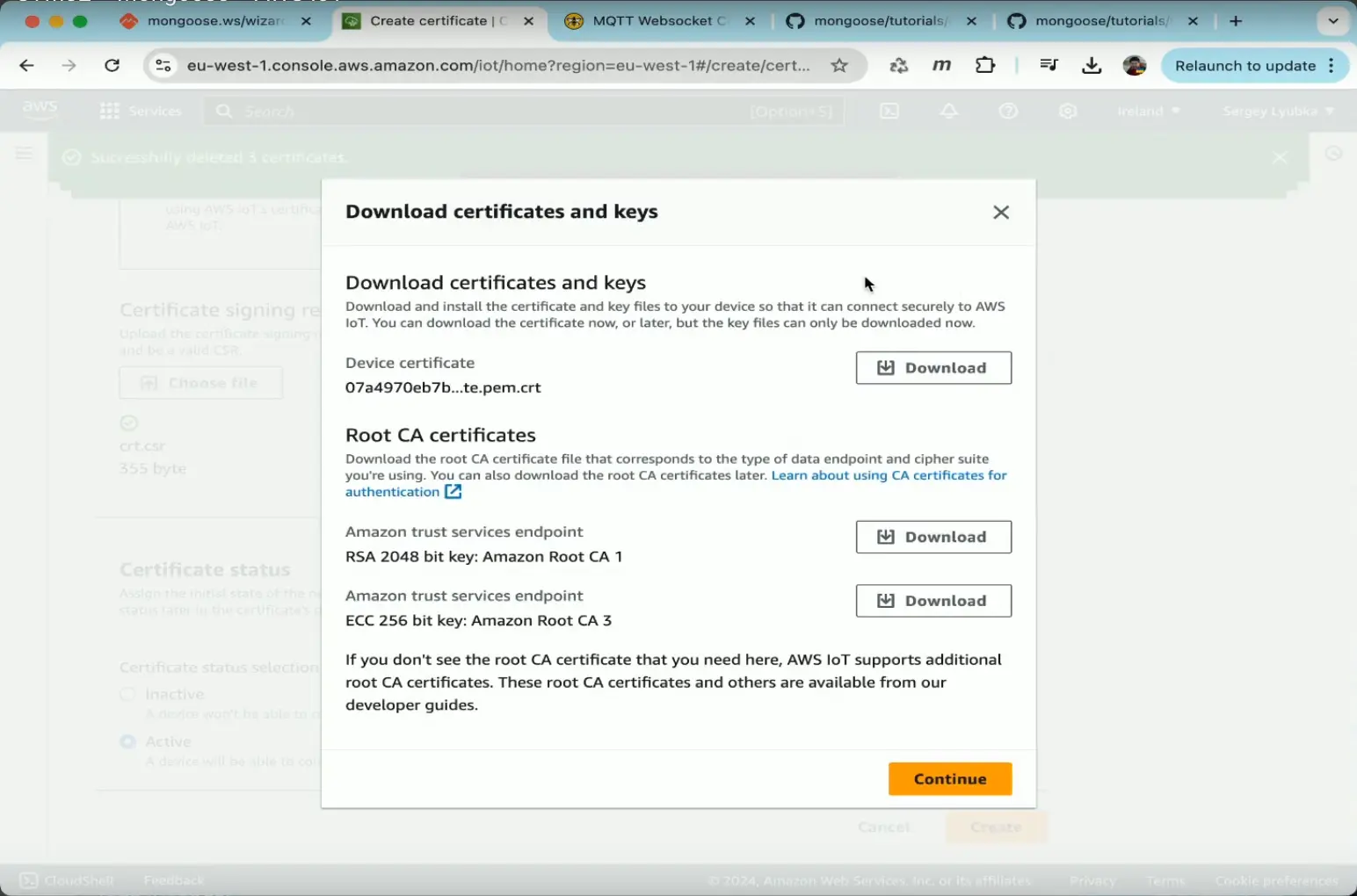
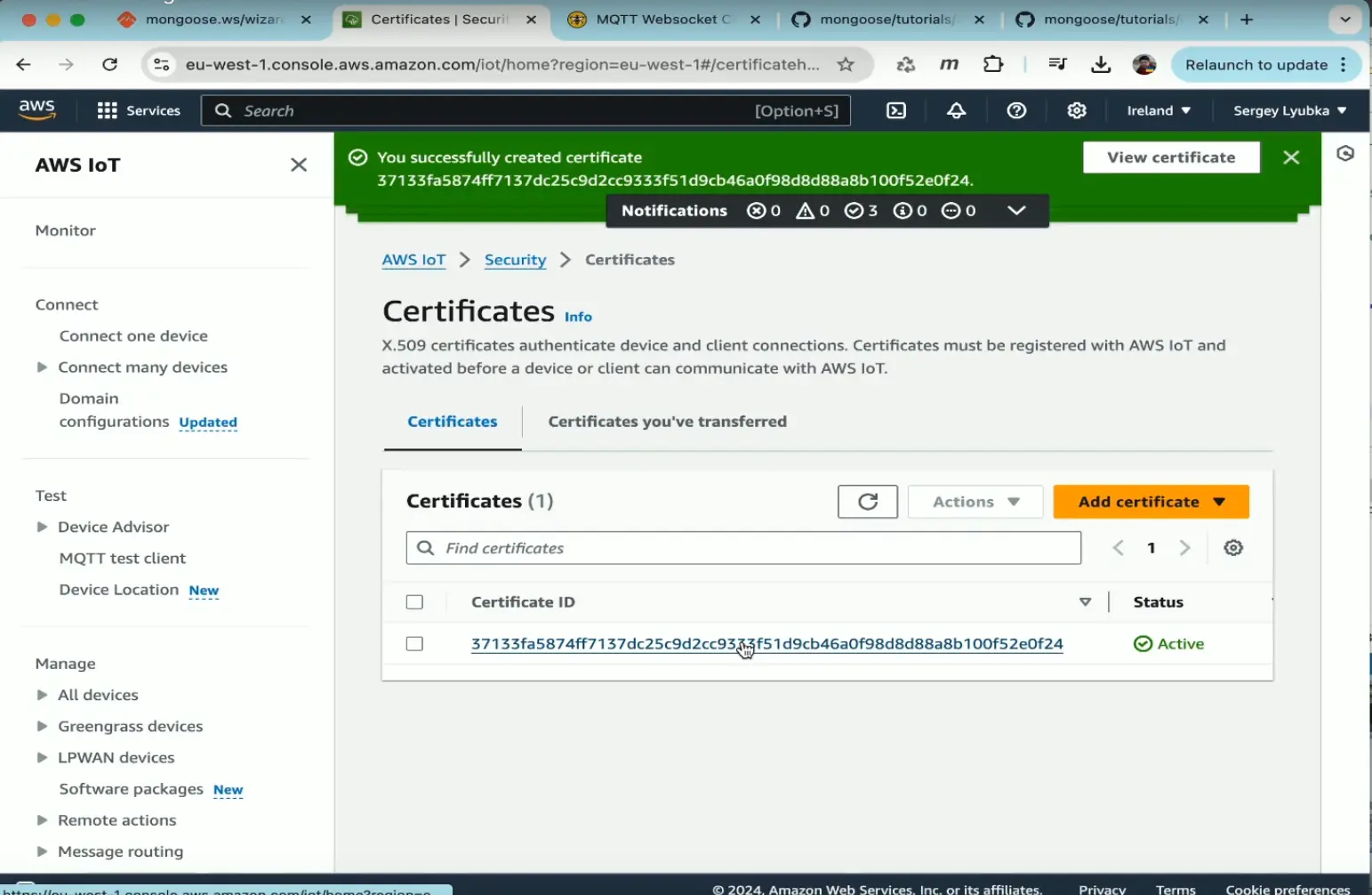
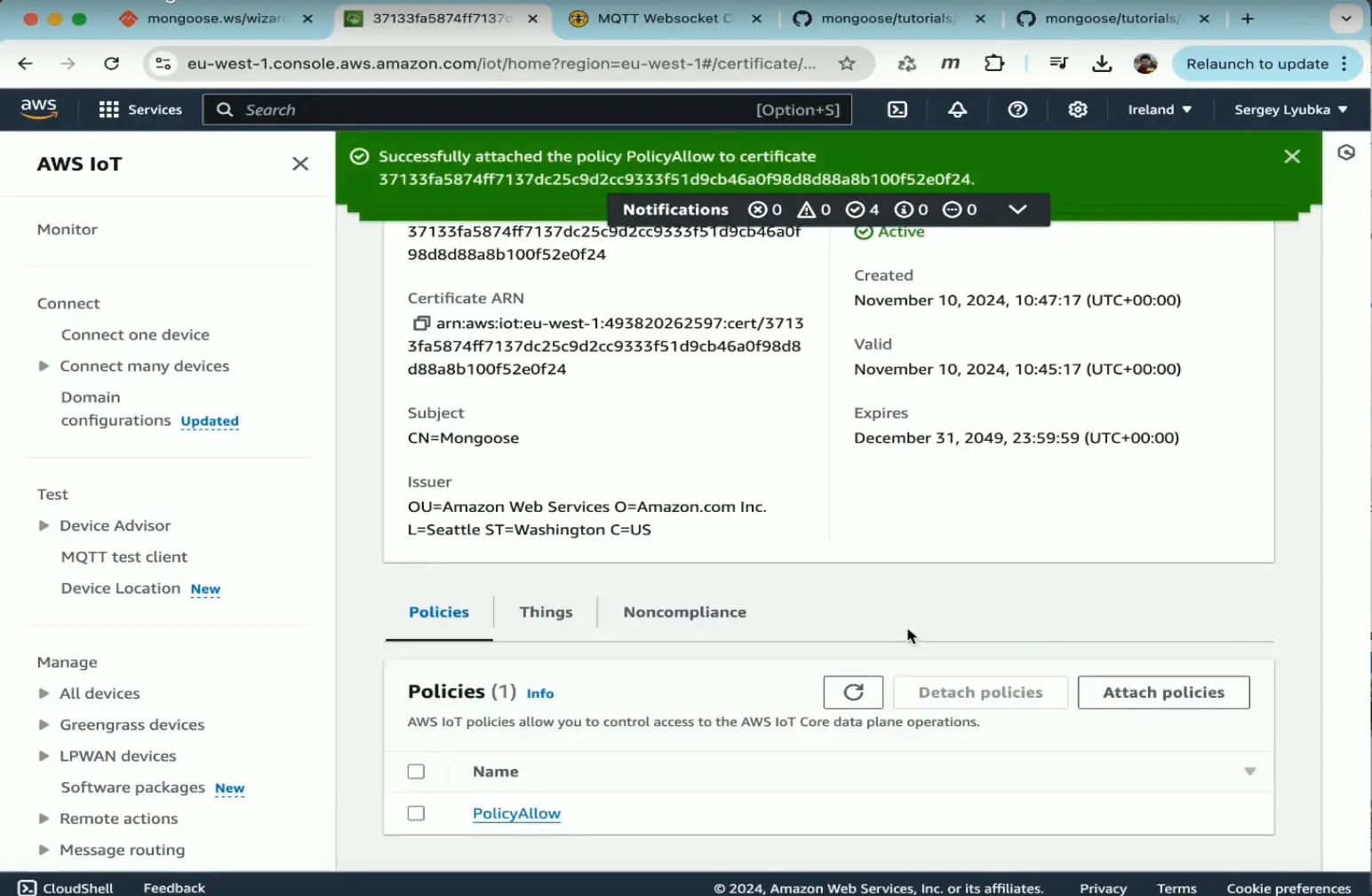
Attach certificate to policy
- Select your certificate, then attach "PolicyAllow" to it
Register your AWS IoT Thing
- On the left bar, click on "Manage" → "All Devices"
- On the right pane, click on Create things → Create single thing → Next
- Enter thing name, for example "thing1", click "Next"
- Attach it to the certificate we created.
Configure MQTT client
- Follow the Build Tools tutorial to setup your development environment.
- Copy
AmazonRootCA1.pemasca.pemto the example directory - Copy
crt.pemandkey.pemto the example directory - Open
main.cand change thes_urlvariable to the actual URL of your AWS IoT domain, we've copied it in the first step. - Build and run the example, check the "How to build" section of the TLS tutorial for specific information on building options for your OS
Testing the MQTT Client
- On the left pane, click on "Test" → "MQTT test client"
- Subscribe to topic
d/tx. You should see test messages appearing - Click on "Publish to a topic". Set topic name to
d/rx, click "Publish" - Check example's log, see that the published message is received
Further information
You can also watch a video of doing something like this using our Wizard for STM32CubeIDE.















 Mongoose
Mongoose